Jump Server
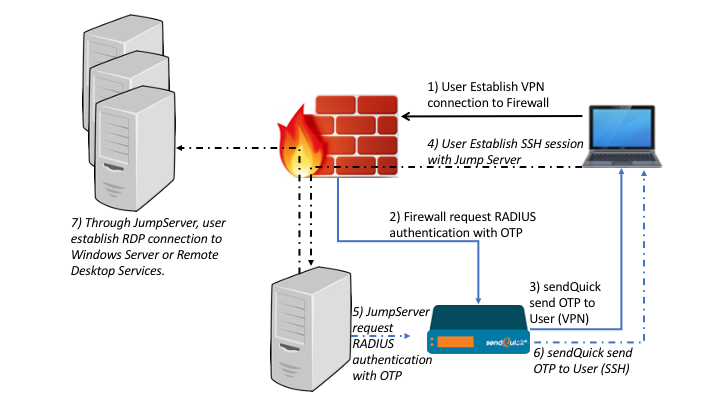
A Jump Server, also known as a Jump Host or Jump Box, is a computer system used to access and manage devices in a separate security zone. It acts as an intermediary or gateway through which administrators can connect to other servers or network devices that are not directly accessible from the internet or an untrusted network. The primary purpose of a Jump Server is to enhance security by controlling and restricting access to critical systems.
Here's how a Jump Server typically works:
Isolation: Critical systems, such as databases, application servers, or network devices, are placed in a separate, secure network zone. This is often referred to as a "management network" or "administrative network."
Access Control: Direct access to the critical systems is restricted. Instead, administrators connect to the Jump Server, which is the only system allowed to communicate with the devices in the secure zone.
Authentication and Authorization: The Jump Server enforces strong authentication measures, such as two-factor authentication, and ensures that only authorized users can access it. Once authenticated, administrators can use the Jump Server to initiate connections to the other systems.
Monitoring and Logging: The Jump Server facilitates centralized monitoring and logging of administrative activities. This helps organizations track who accessed which systems and what changes were made, enhancing security and audit capabilities.
Security Measures: The Jump Server is typically hardened and configured with security best practices to minimize the risk of compromise. This may include regular security updates, firewall rules, and other security measures.
Using a Jump Server adds an additional layer of security to the overall network infrastructure, especially in environments where sensitive information or critical systems need protection from unauthorized access. It's a common practice in enterprise networks and is often implemented as part of a defense-in-depth strategy.
Thank you.