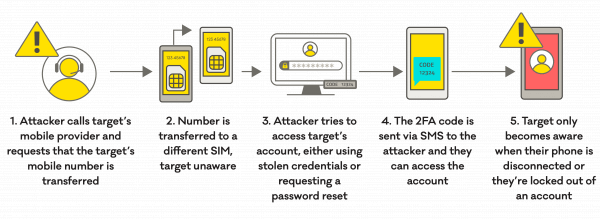
SIM swapping is a type of social engineering attack in which an attacker convinces a mobile carrier to switch the target's phone number to a new SIM card under the attacker's control. This can be a precursor to various types of fraud, including unauthorized access to the victim's online accounts.
The stages of SIM swapping typically involve the following steps:
Information Gathering:
Pretexting:
Contacting the Mobile Carrier:
Social Engineering:
SIM Card Replacement:
Unauthorized Access:
Exploitation:
It's important to note that SIM swapping is illegal and unethical. To protect yourself from SIM swapping attacks, be cautious about sharing personal information, enable two-factor authentication methods that don't rely solely on SMS (like app-based 2FA or hardware tokens), and regularly monitor your financial and online accounts for any suspicious activities. Additionally, always be skeptical of unsolicited requests for personal information, even if they seem to come from trusted sources like your mobile carrier.
Thank you.