APM Support Risk Management within the Application Portfolio
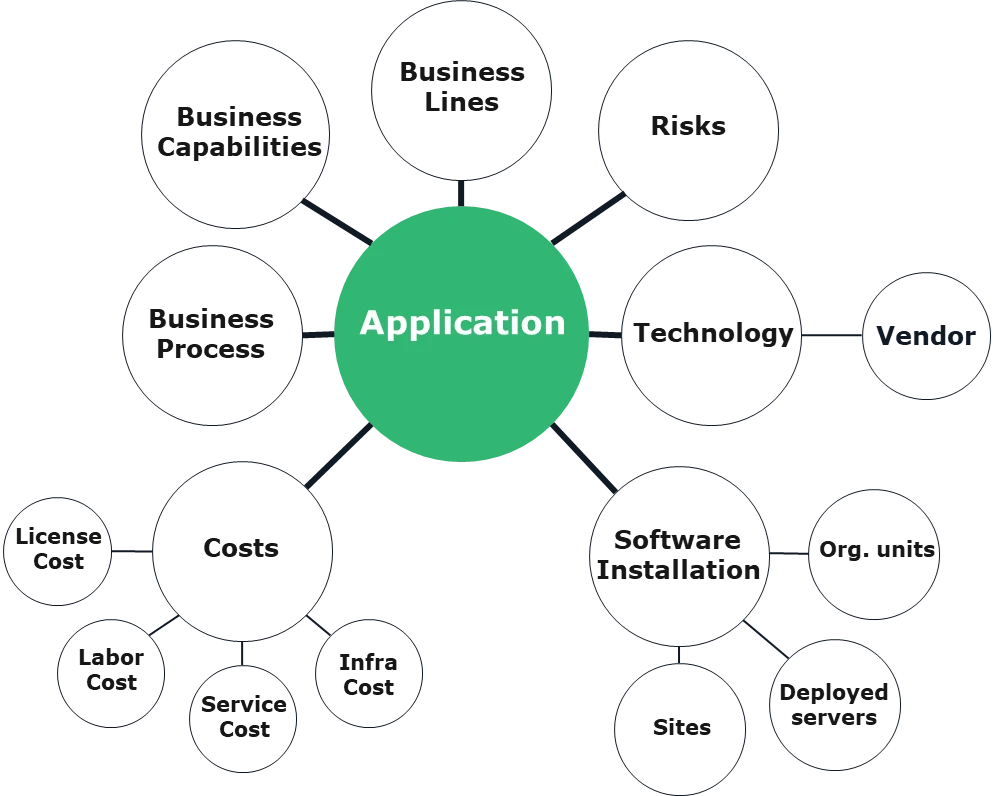
Application Portfolio Management (APM) supports risk management within the application portfolio by identifying, assessing, and mitigating risks associated with applications and their dependencies. Here's how APM helps in risk management:
Risk Identification: APM begins by identifying potential risks associated with applications within the portfolio. This includes identifying security vulnerabilities, compliance issues, technical debt, dependencies on outdated technology, and potential impacts on business operations.
Risk Assessment: APM assesses the severity and likelihood of each identified risk to prioritize mitigation efforts. This involves evaluating factors such as the potential impact on business continuity, data integrity, regulatory compliance, customer satisfaction, and reputation. Risks are categorized based on their severity and likelihood to determine appropriate risk response strategies.
Dependency Analysis: APM analyzes dependencies between applications, infrastructure components, data sources, and external systems to understand the interconnectedness of the application portfolio. This helps identify potential points of failure, single points of failure, and cascading effects that may result from failures or disruptions in one part of the portfolio.
Compliance Management: APM helps organizations ensure compliance with regulatory requirements, industry standards, and internal policies governing application security, data privacy, and IT governance. This includes conducting regular compliance assessments, implementing security controls, and addressing gaps in compliance to mitigate regulatory risks.
Security Vulnerability Management: APM helps organizations identify and mitigate security vulnerabilities within the application portfolio. This includes conducting vulnerability assessments, implementing security patches and updates, and establishing secure coding practices to reduce the risk of security breaches, data breaches, and cyber attacks.
Contingency Planning: APM assists in developing contingency plans and response strategies to address potential risks and mitigate their impact on business operations. This may include establishing backup and recovery procedures, disaster recovery plans, business continuity plans, and incident response protocols to minimize downtime and ensure rapid recovery in the event of disruptions.
Risk Mitigation Strategies: APM helps organizations develop and implement risk mitigation strategies to reduce the likelihood and severity of identified risks. This may involve implementing technical controls, process improvements, redundancy measures, and risk transfer mechanisms to minimize the impact of potential risks on the organization.
Monitoring and Reporting: APM involves continuous monitoring and reporting of risks within the application portfolio. This includes tracking key risk indicators, monitoring changes in the risk landscape, and providing regular updates to stakeholders and decision-makers. By maintaining visibility into risks and their status, organizations can proactively manage and mitigate potential threats.
Overall, APM supports risk management within the application portfolio by identifying, assessing, and mitigating risks associated with applications and their dependencies. By implementing risk management practices as part of APM initiatives, organizations can enhance the resilience, security, and stability of their application landscape while safeguarding against potential threats and disruptions.
Thank you,