Stream Cipher
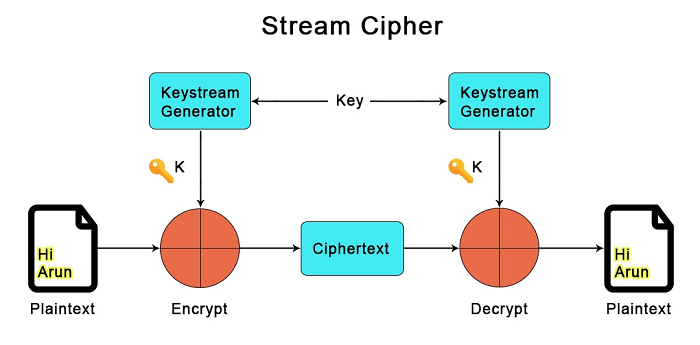
A stream cipher is a type of cryptographic algorithm used for encryption and decryption. Unlike block ciphers, which operate on fixed-size blocks of data, stream ciphers encrypt and decrypt data continuously, one bit or one byte at a time, as a stream of data flows through the algorithm.
In a stream cipher, plaintext is combined with a pseudorandom stream of bits, called the keystream, using a bitwise operation (typically XOR) to produce ciphertext. The keystream is generated by a keystream generator, which typically uses a secret key as input.
Key characteristics of stream ciphers include:
Keystream Generation: Stream ciphers use a keystream generator to produce a sequence of pseudorandom bits or bytes. This keystream is combined with the plaintext to produce ciphertext.
Synchronization: Both the sender and the receiver must be synchronized with the same keystream generation process. Any discrepancy in synchronization can lead to errors in encryption or decryption.
Efficiency: Stream ciphers are often designed to be efficient in terms of computational resources and memory usage. They can be well-suited for applications with high-speed data transmission, such as real-time communication or streaming media.
Key Length: The security of a stream cipher depends on the length and randomness of the secret key used to generate the keystream. Longer keys generally provide stronger security against cryptanalysis.
Security: Stream ciphers are vulnerable to certain types of attacks, such as known-plaintext attacks and chosen-plaintext attacks, especially if the keystream is reused or predictable. Therefore, careful design and implementation are crucial to ensure the security of stream ciphers.
Examples of stream ciphers include:
RC4: RC4 is a widely used stream cipher known for its simplicity and speed. It was developed by Ron Rivest in 1987 and was initially used in the encryption of wireless networks (WEP) and SSL/TLS protocols. However, due to vulnerabilities in its key scheduling algorithm, RC4 is now considered insecure and deprecated in modern cryptographic applications.
ChaCha20: ChaCha20 is a stream cipher developed by Daniel J. Bernstein. It is designed to be highly secure and efficient, making it suitable for use in various cryptographic applications, including internet protocols like TLS and SSH.
Salsa20: Salsa20 is another stream cipher developed by Daniel J. Bernstein. It is closely related to ChaCha20 and shares similar design principles. Salsa20 is known for its speed and simplicity, as well as its strong security properties.
Stream ciphers are used in various cryptographic protocols and applications, including secure communication, disk encryption, and secure messaging. However, they require careful design and implementation to ensure that they provide adequate security against potential attacks.
Thank you,